The NFT space is getting hotter and hotter by the day. Just 124 days ago, you could have bought a Bored Ape Yacht Club NFT for around $189.57 USD plus around $40 in gas on the Ethereum blockchain. Today that single NFT is worth over $120,000 with the current floor price of around 38 ETH. That is fucking astronomical! That is a life-changing amount of money for most people.
With astronomical gains comes the irresistible call to the darkest parts of the interwebs who want to take everything they can get from you, and they will.
Blockchain technology and removing the middle man makes YOU responsible for your own security. There is no customer service you can call to reverse a mistake you made so pay attention. I am going to go through some of the top scams I have identified and share some common sense tips to hopefully help you stay safe from the spider’s web of scams just waiting for you.
1. Never FUCKING EVER share your seed phrase with anyone, EVER!
Metamask support will NEVER ask you for your seed phrase. I don’t care if Jesus Christ himself comes down and asks you for your seed phrase, thou shalt NOT tell Jesus, Mary, Joseph Jehovah, Gandhi, Buddha, your therapist, or your favorite rapper any of those 12 or 24 words included in your seed phrase. Do I make myself clear?
Anyone with that set of words has full access to all of your assets. Anyone asking for that seed phase is 11,999% going to steal any money or assets you have associated with that wallet.
- WRITE DOWN your seed phrase and keep it in a safe place, write it down twice and keep it in two separate places
- DO NOT take pictures of your seed phrase, private keys, or mobile sync QR code and store this on your phone or worse than that send it to yourself via email, text, or save it on your computer if it’s connected to the internet and in digital form, it is liable to be sniffed out in some way.
- WRITE. IT. DOWN. Seriously, do not be lazy this could cost you millions of dollars in the future.
Consider the enhanced security of a hardware wallet connected to your Metamask like a Trezor or Ledger Wallet but ONLY buy them from their official websites NEVER buy from Amazon or some other third party, because wallets can come tampered with from untrusted sources.
-
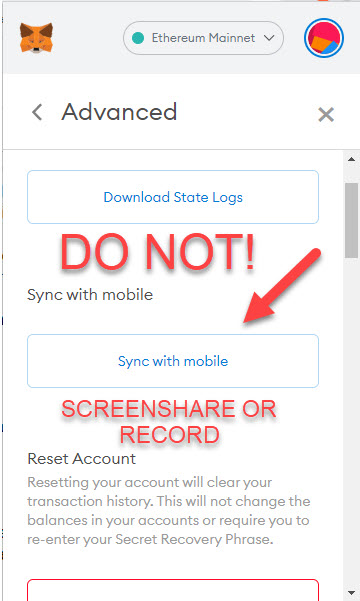
Do NOT EVER share your screen and click on sync with mobile under your Metamask Settings!
A newer social engineering exploit that has been very successful for scammers is they prey on people looking for help with Metamask, especially on Discord or Telegram groups.
They will pose as the admins of the group as they are able to spoof or fake the usernames in those applications so you think you are speaking with someone trustworthy, but you are not and they are about to rob you while you help them do it.
If you click on your Metamask settings > Advanced > and then “Sync with Mobile” while sharing your screen, congratulations you have just been robbed, and you helped them.
The scammers now have full control of your funds and assets and will remove them as quickly as possible maybe even right there in front of your face during the screen share.
They may even be more clever and wait till later while you are sleeping and siphon everything of value out of your account.
Sync with mobile is supposed to be a convenient way to sync your Metamask wallet with your phone, but if someone else is watching and gets even just a millisecond glimpse at the QR code that comes up on the screen, that account is now fully compromised, and you just got robbed.
Metamask needs to do a better job of WARNING people before they press the sync with a mobile button instead of showing the warning with the QR code already on the screen. Big RED Flashing screen that says can anyone see your screen right now? If so, DO NOT click this button; this could be solved with a better user interface.
Read this awful story below of how this just happened to someone. They stole over 250 ETH in valuable NFTs worth nearly $1,000,000…
I know 2 other people personally who have fallen for this as well. The worst part is that they were experienced and knew how important security is in this space, but still fell for it.
Often times during a moment of panic, or frustration, or trying to solve some problem with a transaction is when you don’t catch the tiny little detail that ends up costing you dearly.
-
How to Spot Possible Scam NFT Projects
To understand this part I will need to explain a few things that may sound nerdy but could save you THOUSANDS of dollars in fake NFTs. There are two main types of smart contracts on popular NFT marketplaces. They are:
- Shared Contracts
- Custom Contracts
One is superior to the other HANDS down, don’t let ANYONE at any marketplace tell you any differently, no matter how smart they sound. It’s all about transparency.
Shared contracts are inferior to custom / verified contracts in almost every way.
Opensea is the largest NFT marketplace and everything minted on Opensea is done so in a shared contract and while there are some cost benefits to dumping all the NFTs into one single large collection in one contract, there are some serious downsides for artists and collectors to consider.
![]()
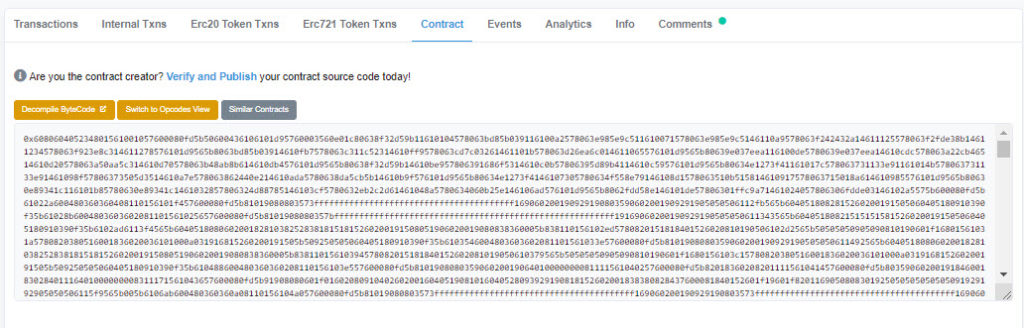
This is what a shared non verified open sea contract looks like in Etherscan:
This is how you find the contract link on Opensea:
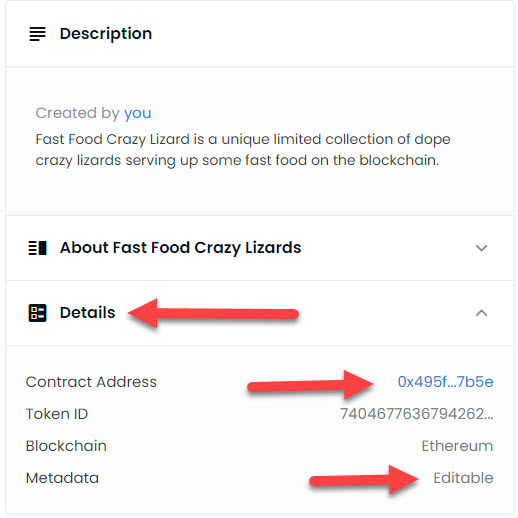
Where you see “editable,” or it will say “centralized,” this means it is an Opensea Shared Storefront contract. You can click on the contract address, and it will take you to Etherscan.
Custom Contracts are Better and the Details are different:
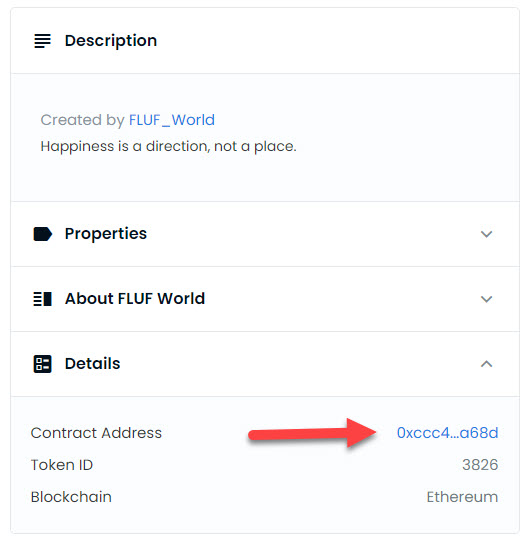
When you click the contract address it will take you to Etherscan, and on the right-hand side of Etherscan, after clicking on the contract address again, you will see the token tracker name of the custom contract.
![]()
Here is what a custom contract that is verified looks like. (Green check means verified):
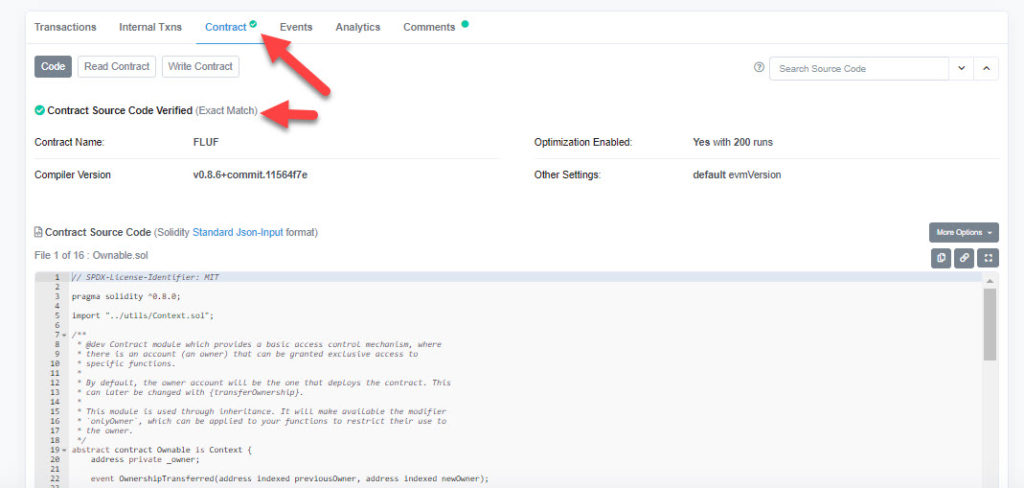
Now, do you see some of the major differences? For one, a custom verified contract can be read by a human. People a lot smarter than you and I can read through them and verify what the smart contract actually says. Although with just a little digging, you can learn to read even just basic things in a smart contract as well.
The ability to lazy mint into shared contracts is one of the reasons they are so widespread. However, that free minting comes at a cost to you as the artist, and to your collectors.
For the minting of derivative projects where you have the rights to another NFT you hold such as a Bored Ape or any of the number of avatar NFT projects using a shared contract could be okay to use. However, if you are building a more serious project or buying into one, especially for collectibles, you should definitely insist on using a custom contract. For projects that use custom contracts, that is the number one easiest way to spot a fake NFT because the fakes use shared contracts.
For every major NFT drop there are always fakes being uploaded as soon as the project drops on Opensea and they almost always exclusively use OpenSea Shared Storefront contracts to create the fakes.
This is one of the many reasons why any serious collectible NFT project should be using a custom contract so that your collectors can quickly identify the authenticity of your project.
There are additional benefits to having your own custom contract for you and your collectors to include full visibility into the holders and token distribution of that NFT. This is very important for serious collectors and a good way to spot if an NFT project team is telling the truth about certain things that can be proven or disproven on the blockchain.
4. Always verify an NFT projects Contract address from an official source such as their website or in the announcement channel of their discord
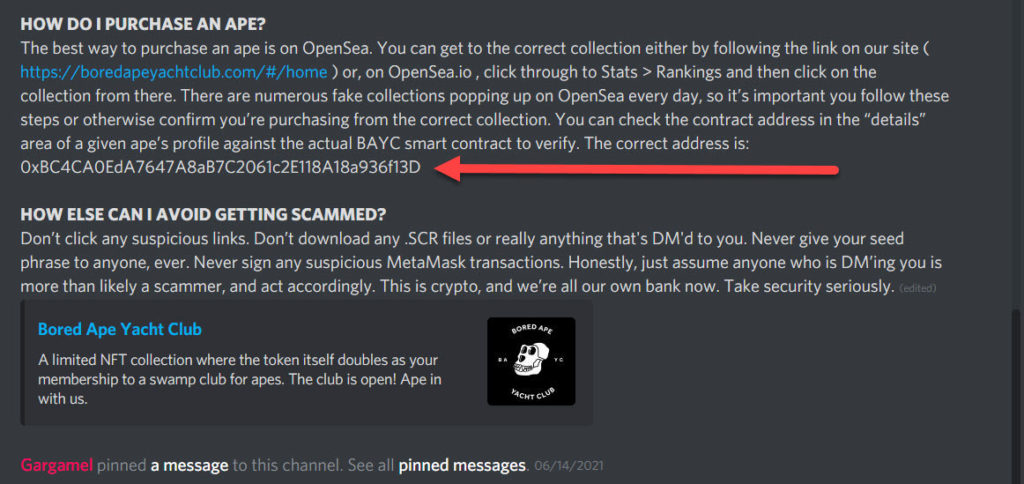
Copy and paste the contract address being pointed to by the red arrow above into https://etherscan.io/
You will then see this below:
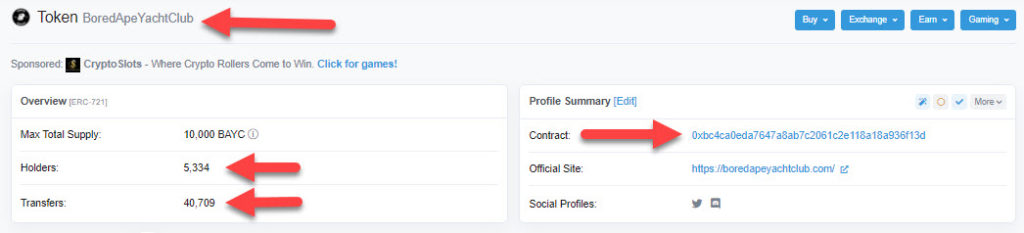
If you click on the contract (red arrow on the right side) you will see where it says, token tracker as shown below:
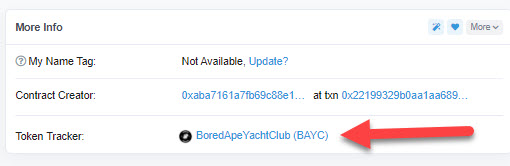
-
Verify Opensea Collection links from OFFICIAL SOURCES and TRIPLE CHECK THEM
You should be getting the OpenSea collection links only from the official website of the project and the announcement channels in the discord servers where ONLY Moderators can post.
There will often be a number of scammers in the discord server sharing fake links to get unsuspecting people to click and buy fake NFTs from fake collections. This is why checking the details section and seeing a custom contract versus an opensea Shared contract matters, and why if you are serious about collecting a project ensure they understand the difference between shared contracts and that they are building their project on its own custom contract.
This is how sneaky these scammers are, look at these two opensea collection links below:
![]()
![]()
One is real and one is fake can you spot which one is fake?
I’ll give you a hint look at how the word “battle” is spelled in the first link, that’s the fake one.
What makes this even worse is that I found this in an NFT bundle where someone was selling 5 of these Baby Battle Bot NFTs for .88 ETH which seems like a steal because each one was going for around .24 ETH right after the drop and, in my excitement, I shared this link to the bundle below with friends who were looking to buy several because the project looks so promising.
https://opensea.io/bundles/5-baby-battle-bot-UvS (SCAM BUNDLE)
Only if you knew to look at each of the 5 NFTS in the bundle would you have spotted the above difference in the links and seen that someone paid .88 ETH for 4 FAKE NFTS and only 1 real one, this could have been one of my friends had I not checked each NFT in the bundle and spotted the fakes and told them immediately.
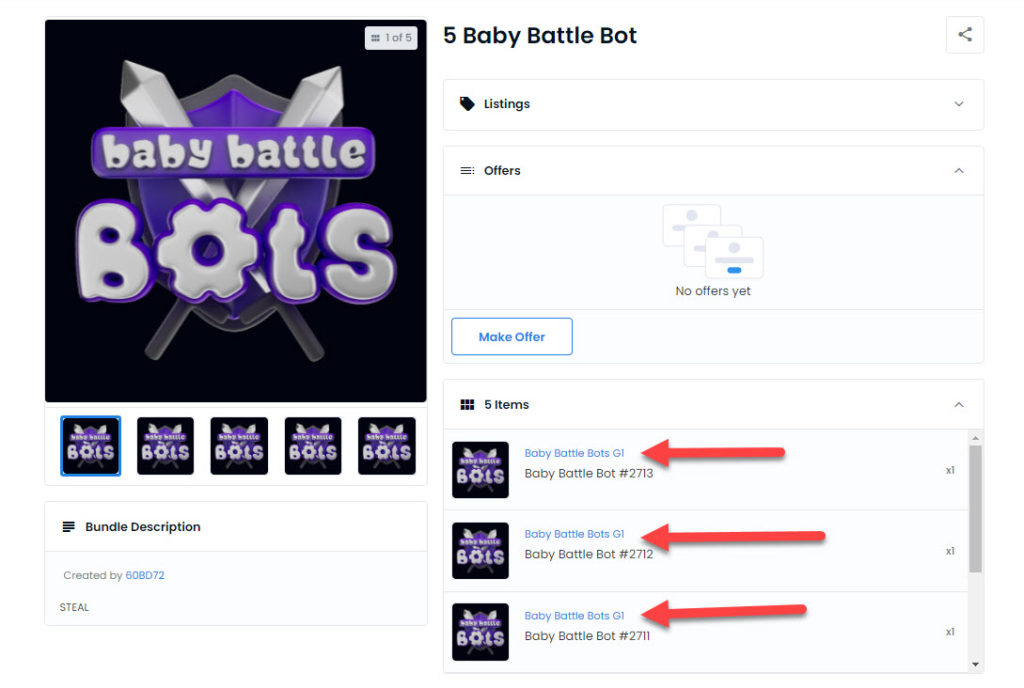
-
Assume everyone you don’t know is a potential adversary looking to take something from you, so proceed with caution.
Here are some basic tips
- Don’t click on links from people you don’t know
- Don’t open files and attachments from people you don’t know.
- Discord Server Mod usernames can be faked easily (DISCORD GET YOUR SHIT TOGETHER AND FIX THIS)
- Don’t leave the discord server you are in to go to a “support server” this is most likely a scam and they will socially engineer your money away from you.
- Don’t send funds or NFTs without using a trusted service like NFTtrader.io, SudoSwap.xyz , swap.kiwi, or on Opensea where you can list an NFT for sale for super expensive (so no one accidentally buys it) and give the person looking to buy the NFT from you the link where you accept an offer they make for that specific NFT. In this process, you will need to know their address or Opensea username in recognizing the offer.
- Use common sense
- If you don’t know or are not sure, don’t be shy and ASK someone you trust that knows more than you do.
This concludes today’s lesson on how to spot scams in the NFT Space, your welcome! I hope this helps you keep your money and assets just a little bit safer.
I made this video walkthrough below for you all who are too lazy to read this all the way through and don’t pay attention to the details. I will say, the number one way you will get scammed is not paying attention to the details. So learn to pay attention because the details matter very much in this space.
Remember only you can prevent the theft of your Metamask wallet assets.
If at any point your seed phrase is exposed, consider that wallet fully compromised. You can never use that wallet ever again. And if they haven’t already robbed you, then you will need to remove all valuable assets from this wallet as soon as possible.
The problem is that the scammer could be waiting for you to transfer funds into the wallet or see the movement of the assets before making a move. For example, if you have a lot of NFTs it will cost gas to move those NFTs. If you transfer in a lump sum of money to try to transfer them out, they could be waiting for that, and swipe those funds.
You do not want to be in this situation trust me. Paying attention to security and understanding the details is important to staying safe in this crazy NFT space.