Since at least June 8th, a number of crypto artists have announced on Twitter that they were tricked into downloading malicious files because they believed that they were being contacted via social media for art commissions. The combination of social engineering and software hacks led to the loss of untold sums and NFTs to the attackers. A great deal of information was shared on Twitter about the attacks and a number of brief guides to improve NFT security were shared by artists and their allies as well.
Early Warning
Perhaps the earliest alert came from artist Suryanto Sur who posted on June 8th that not only was his wallet hacked but that the attackers were sending additional threats and demanding a ransom:
Dearest collectors and friends, my wallet has been hacked. I agreed to do a commission for someone who sent me a file to download, and it gave them access to everything. They have threatened me and my family. pic.twitter.com/XVfYQeglMN
— Suryanto Sur (@Suryanto_sur234) June 9, 2021
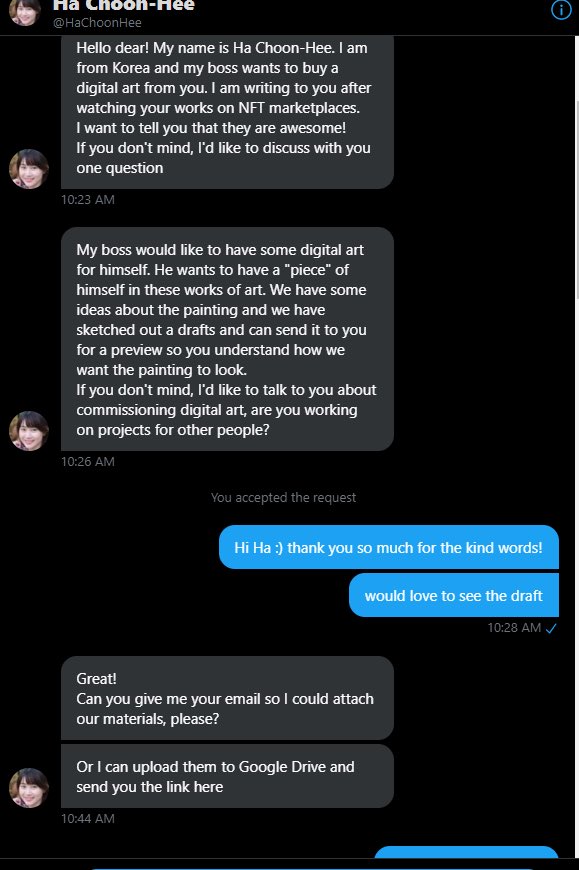
This dramatic news first appeared to be an isolated horror story, but was soon revealed to be an early warning of widespread attacks. Though the details varied, the essential plotline involved outreach for an art commission, whether corporate or personal, followed by a link to a zipped file on Google drive. Once the file was downloaded and unzipped, it revealed an SCR file that unleashed a software attack allowing the hackers to access passwords and other sensitive information. Attackers stole money and NFTs and often demanded ransom payments.
Spreading the Word
On June 11th, three days after the attack on Suryanto Sur, FVCKRENDER announced that he too had been attacked via a similar scenario (see also featured image above):
Be really careful out there I was dumb enough to not overlook this and open their SCR file and got my metamask swiped from à to Z all my tokens gone. They tried to access other app but my 2fa blocked them to. I’m an idiot don’t me an idiot like me and secure your shit. pic.twitter.com/gAins00taH
— FVCKRENDER (@fvckrender) June 11, 2021
Based on a large number of retweets and responses, this announcement seems to have gotten the most attention, and alerted a wide range of artists to the ongoing threat. However, this writer observed, even after numerous alerts, multiple new announcements by artists who had just fallen prey to the scam proved that they were unsure of what to do and were reaching out for help on Twitter. In addition, it seems some thought the first attacks occurred on June 11th based on the visibility of the attack on FVCKRENDER.
As both RenderedFlesh and Pascal Marsolais pointed out, one important community defense is to share news of such attacks to raise awareness regarding current tactics as well as to encourage additional self-education over the long-term. This approach ultimately succeeded but the unfolding of events raises the question of whether or not earlier widespread sharing of alerts might have reduced the number of victims.
Catching Our Collective Breath
There were also lighter moments in the midst of what were real tragedies for many artists. Squirterer shared a number of screenshots and a description of her process of toying with one of the attackers leading to a humorous punchline.
SP4CE passed along a piece by Jeremy Torman describing how he “turned a scammer into an art collector.” His account of scamming the scammer for 0.1 ETH via an art sale is a humorous reminder that crypto artists don’t have to live in fear if they maintain consistent awareness of possible threats and act accordingly.
NFT Security Practices
As many have noted on Twitter, scams that convince individuals that the scammer is on their side and has good news have a long history; as do the use of such executable files as SCR. Such threats have been particularly common, though not limited to, Windows users. And some feel that everyone should already be aware of the situation. To a large degree, the positive response of so many artists to commission offers speaks to the power of a well-chosen psychological point of entry into the victim’s world.
Manifold, a company that provides NFT minting services to crypto artists including FVCKRENDER, reached out and supported the artist in the wake of the attack. Manifold shared a postmortem with additional technical details and advice.
Manifold’s suggested best practices include:
- Use a hardware wallet.
- Do not store seed phrases on digital devices in plain text.
- Use password managers rather than saving passwords in browsers.
- Enable 2FA on all accounts.
Additional threads and links to articles on NFT and wallet security were shared by individuals on Twitter including:
Bharat Krymo also shared relevant crypto security tips prior to this wave of attacks.
However, as in all areas involving critical information, DO YOUR OWN RESEARCH. Studying advice from multiple sources can not only reveal established best practices, but can also reveal when some advice has become outdated. In addition, relatively timeless practices, such as not downloading files from strangers, will be communicated to your unconscious brain causing you to develop better security intuition as well.
Next Steps
As NFTS WTF DAO member Sillytuna points out, there are a variety of steps the NFT industry and adjacent companies could be taking to support the security of artists and collectors:
Artists need to be moving to hardware wallets. It's a not a cure all but I've worried about artist reliance on metamask etc for months. Stores need to stop relying on single addresses for identity as that encourages poor security.@opensea @dan_OpenSea @rariblecom @withFND etc
— Sillytuna (@sillytuna) June 11, 2021
Industry associations like the Blockchain Game Alliance might put effort into establishing higher security industry standards across platforms as well as joining together in educational efforts.
We should also be contacting relevant web services and government agencies when events like these occur such as SamuelCardillo.eth notes. Though not all services and agencies will be responsive, keep in mind that we must educate them as to our concerns, and be sure to document all contacts. Such records may be useful at a later date, for example, when speaking with the press or doing follow-up reports. Note that Mintable reached out to help with information for law enforcement agencies.
The most effective response to date to attacks like those recently hitting crypto artists is for the community to rapidly spread the word when new waves of attack occur and to share educational resources. We must continue to remind newcomers of best security practices, even when such practices seem well-established and obvious, so that they might take appropriate steps. And, in all cases, we must encourage each other to DYOR in NFT Land just as we do in other settings in which we find ourselves vulnerable to malevolent forces.
[Featured image via FVCKRENDER]